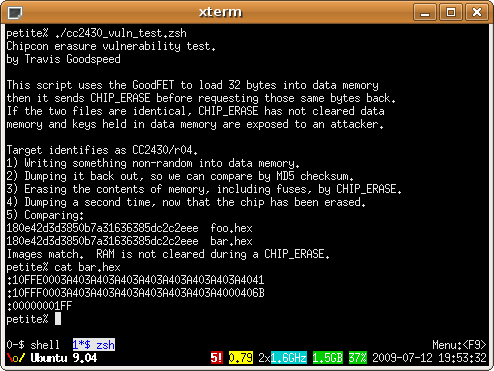
Last week, at Black Hat Briefings, I presented a short paper entitled Extracting Keys from Second Generation Zigbee Chips. Though brief, the paper is vitally important reading for anyone shipping a product with chips from Chipcon and Ember. The paper includes a method by which keys may be extracted from these chips, as well as a software method for defending Chipcon devices against the attack. All EM2xx chips are vulnerable, as are all of the 8051-based Chipcon radios, such as the CC2530. This is not the same as my attack against first generation, discrete radios.

11 comments:
brief of the paper is really vitally important reading for anyone shipping a product and you role is kind an important in this shipping product I give suggestion that you have to take help from MBA Assignment Writer in making you greatest work.
Thanks for this post. Looking for the best nursing assignment help UK just make a call to Assignments Planet for professional assistance and fast turnaround time.
thanks for this informative content
I am a skilled essay writer and working with Business assignment writing help for the past 4 years
Working on any research paper always presupposes spending a huge number of resources, such as time, health, efforts, etc. In addition, you need to carry out research, conduct experiments, create a summary with the results and write a huge amount of text about the background and importance of your research. Order it online if you started it and realize it's an unbearable task. Here's a service
custom coursework writing, providing students with outstanding academic help. If you doubt whether this help is legit or not, just visit this website and find all information on this topic you need.
"Extracting Keys from SoC Zigbee Chips" Thanks for sharing the informational blog.
How To Get Girls To Chase you
In Perth, CPR refresher courses offer vital skills updates for individuals seeking to maintain their life-saving capabilities. These courses, typically lasting a few hours, focus on cardiopulmonary resuscitation (CPR) techniques, ensuring participants are well-versed in the latest protocols and best practices. Facilitated by certified instructors, these sessions cover critical aspects such as chest compressions, rescue breaths, and proper use of automated external defibrillators (AEDs).
Participants engage in hands-on practice, fostering confidence and competence in emergency response situations. CPR refresher course perth play a crucial role in empowering individuals to respond effectively to cardiac emergencies, contributing to a safer community.
When it comes to jewelry stores , Jewelgalore stands out as a premier destination. Discover a diverse selection of beautifully designed pieces, reflecting your unique fashion sense with elegance and grace.
The distribution of firmware, much like the GoodFET project mentioned here, plays a crucial role in the world of cyber security. It's fascinating how something seemingly benign can be exploited, much like in the case of Josh Baazov. Baazov's name became infamous not just for his financial ventures but also for alleged involvement in hacking and cyber crimes. This serves as a reminder that security in tech isn't just about building strong defenses, but also about ensuring that those who develop and distribute technology do so with integrity and responsibility. Understanding these complexities is key in navigating today's digital landscape.
There's so much updates from computer software nowadays.
HVAC Surplus Parts | Discount HVAC Equipment
I've got a basic knowledge about it.
Aqualine Steel Rainwater Tanks
Understanding the Australian criminal law system was quite a task during my university course. I discovered criminal law assignment help in Australia, and it turned out to be a game-changer. Their experts are well-versed with local legal frameworks, making it easier for students to meet academic requirements. The service was punctual, affordable, and really helped me score better in my assessments. Great resource for Aussie law students!
Post a Comment