I'm working on a pair of hands-on Zigbee hacking workshops. The first, which I've submitted with Aurélien Francillon to ToorCamp involves the writing of advanced stack overflow attacks for the MSP430 and AVR microcontrollers. The second, which I've submitted to Defcon 17, involves a number of hands-on hardware attacks against Zigbee nodes. Both include the sniffing of AES128 keys from a CC2420 Zigbee radio, a procedure that I demonstrated informally at Source Boston and describe below.
The CC2420 is a popular Zigbee/802.15.4 radio, and it is found in many wireless sensor development kits. We'll be attacking its hardware-accelerated AES128 implementation, by taking advantage of the fact that keys must be loaded over the SPI bus.
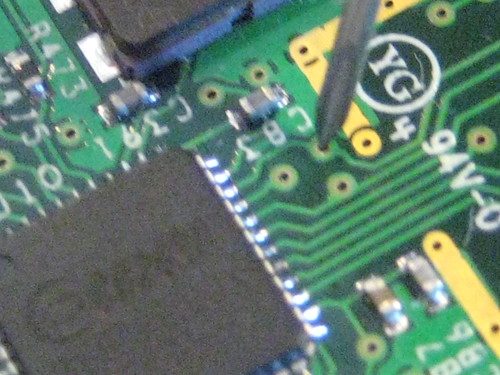
In the photograph above, I've tapped one of three SPI pins of the CC2420 radio chip on a Telos B using a hypodermic syringe. SPI consists of four pins: SCL, MOSI, MISO, and !SS. SCL, the Serial Clock, is output from the master to synchronize communication with the slave. MOSI and MISO are data lins, Master Out Slave In and Master In Slave Out. !SS or Slave Select is an inverted line that indicates the selection of a particular slave chip. Here, we'll only be tapping SCLK and one of the data lines, as two syringes are much easier to hold that four. Ground is shared by USB, so it isn't critical that we tap it.
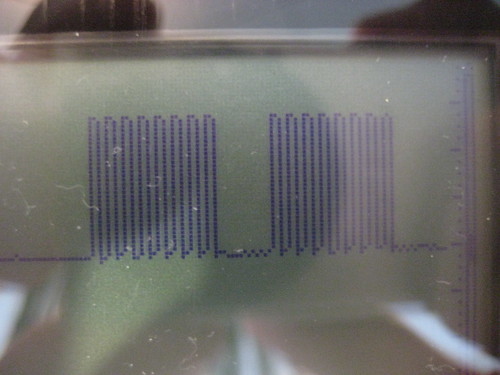
As seen on my portable scope below, the tapped pin is the SCL, the data clock. The clock stands out because it idles low, and because all pulses in a batch are of regular width. Unlike a system clock, the clock only cycles when data is being transported.
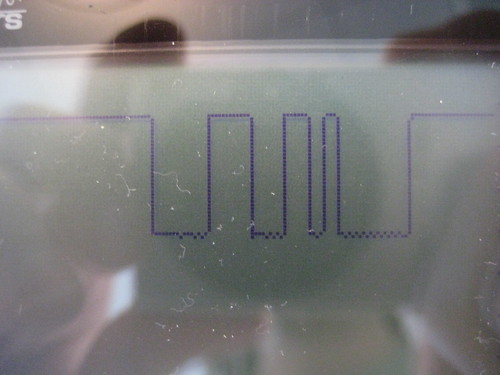
The remaining two pins, in the group of three, are data. As shown on the scope image below, SPI data lines idle high, and bits are measures on edges of the clock.
Now that the clock and data lines have been found, it is necessary to sniff the traffic using a bus adapter. Until SPI-sniffing firmware for the Hackaday Bus Pirate becomes available, I will continue to use the Total Phase Beagle I2C/SPI Protocol Analyzer. A screenshot of the Total Phase client follows.
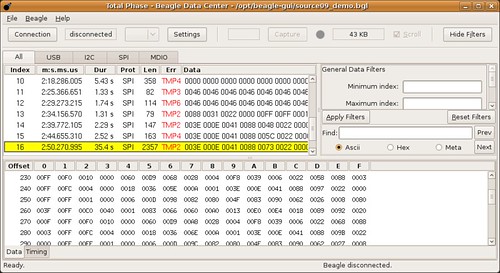
All that remains to identify the key in use, or anything else sent over the bus, is to read the log. I will likely release scripts for doing so at Defcon.

38 comments:
This is a side channel attack and thus doesn't constitute 'breaking 802.15.4 AES128' per se as it is relevant to a specific device
Agreed; interesting, but it's simply about sniffing SPI lines; not 802.15.4. Requires physical access to the device(s).
Yes, I've used a Beagle a few times at work, I really like it. How are sure that you are synchronizing correctly every time without using a slave select (CSn)? I know it can be hard to hold that many probes, but why not just solder a wire down?
I don't think that scope grab is what you are looking for. The AES transactions should have 16 SCK pulses in a row, not 2 bursted 8 SCK ticks. Look at fig 9 of cc2420.pdf, you are going to need the CSn signal to properly frame the transactions.
"All security related data is stored little-endian, i.e. the least significant byte is transferred first over the SPI interface during RAM read or write operations."
Are you setup to have pre-knowledge of the key? How are you going the identify it in the SPI log? The only RAM signal brought out is DVDD_RAM pin. I guess you could current sense and trigger on the RD/WR assuming there is a descernable current spike.
@frankincense
Depending on the firmware running on the MSP430, it may take awhile for the second byte to be transferred to the CC2420. The delay isn't unusual. Also, unless the TelosB external ST dataflash chip is being used (unlikely in many applications, at least during runtime), checking for chip select isn't needed.
Also, identifying the key is trivial - just search for the right ram-write command and the relevant address.
This is of course a problem with any pre-shared key system.
@Yann Ramin,
Ahh, you got me, shouldn't have posted without doing the rest of my homework.
What type of portable scope do you use ?
The ZigBee Smart Energy Profile (SEP) uses certificates for secure communication. Simply knowing the link or network keys is pretty much useless unless you also have a certificate from the licensing body (Good luck, they are a royal pain in the a$$ even to those who are paying their exorbitant fees).
At this point, the vast majority of pilots and products out there that support SEP are based on the EM250, and not the TI CC2420. Utilities are requiring the security and standardization that the SEP provides.
I consider this blog to be cute. However, it has shown that politicians with mediocre minds will over react to anything that serves their purpose.
Hey Travis, whilst I think your efforts to uncover vulnerabilities in systems are applaudable, are you going to quit spreading FUD about how by reading an AES-128 key in a CC2420 "you could control not just that meter you stuck the needle into, but any meter in the system" (http://www.forbes.com/2009/04/29/smart-grid-legislation-technology-security-smart-grid.html?feed=rss_technology_security)?
If not, maybe you could explain how you could do this?
Bruce,
See my paper entitled Extracting Keys from Second Generation Zigbee Chips for details of how to extract data memory from all presently available Ember and Chipcon radios, including the EM250. All of data memory is exposed, making certificates just as easy to extract as keys.
--Travis
free minecraft codes for you my friends.minecraft gift code generator
The Jagannath Rath Yatra is the largest and most visited Rath Yatra in the world. The English word juggernaut was originated from Jagannath which means massive and unstoppable “ratha” carrying Lord Jagannath. Another important feature is, the icon of Lord Jagannath is a carved out of wood and not stone or mud as done in case of usual Hindu deity. Amazing Facts About Hinduism
This guide https://essaydragon.com/blog/why-michigan-essay-guide will help you to write a decent application letter to University of Michigan!
Way cool! Some very valid points! I appreciate you
https://autoxtools.com/
Inspired by grey rain-bearing clouds and a beautiful overcast sky, this bluetooth tracker in Cool Grey auto x tools is made for uber-cool personality
valid
The bohemian style is made from head to toe
point
www.hotmail.com
Я благодарен владельцу этого сайта за то, что поделился этой замечательной работой. Когда у вас есть подключение к Интернету, все, что вам нужно, это браузер, чтобы проверить веб-камеру. Если вы хотите узнать больше о веб-камерах, посетите эту статью тест веб-камеры онлайн .
Yahoo will send you a reset link in your phone number or email address. In case if you are not accessing to the phone number anymore, click on I don’t have access to this phone option. It will then send you the link to your alternative mail address. Check your mail and do the procedure as suggested.
Such a great post many students need this kind of post please keep writing webroot.com/safe is best Installation Guide.The security package offered by this brand is incredibly easy to setup and install. You can easily install and upgrade any of the Webroot Secure Anywhere Antivirus products that help you handle cyber security in the best possible manner.
Download and install or reinstall office setup on a PC or Mac
garmin.com/express is gps tool
which enable you to manage your Garmin GPS device from your computer.
very good post keep writing this kind of postij.start.canon/setup is the easiest way to setup Canon printer to your system. Steps to connect wired or wireless printer on windows as mac devices are discussed below in this article
How to download and install hp drivers from 123.hp.com/setup? You can download hp assistance to auto update drivers without any hadic
If you cannot download or install Norton on your device, read following steps for installing Norton in your PC. Go to the Norton Web link that is norton.com/setup/productkey and then click install button.
pest control service near me professional not just has the most up to date as well as most effective items,however additionally the education and understanding to finish the job right.
123.hp.com/setup ePrint setup · Open any email application, and enter your printer's email address. ·
Attach the document or photo you want to print and send it. ij.start.canon
You can download printer drivers from ij.start.canon/setup and sit at home with free mind.
Use garmin.com/express to update maps and software, sync with Garmin Connect and register your device. This desktop software notifies you when updates. Best
pest control near me but we are professional in this field
The website is looking bit flashy and it catches the visitors eyes. Design is pretty simple and a good user friendly interface.Virus Disinfecting Services Pageland
Launch a web browser. Enter the Belkin router website link or the router's default IP address, 192.168.2.1, in the Address bar and press [Enter]. If it doesn't work, check your router's IP address. You will be asked to log in using the router's admin password. If you have not set a custom password, just leave the Password field blank then click Submit.
It's very nice article. I like the post so much. Thank you!
download igoal
This is very interesting content! I have thoroughly enjoyed reading your points and have come to the conclusion that you are right about many of them. You are great. best cbd shop near me
We exclusively offer bespoke and top Australia Assignment Help to overburdened understudies struggling to make scholastic ends meet and help them score top grades consistently.
There are multiple Best Places to Visit in Gurgaon; thanks to the number of party places where you can hang out with your friends at the weekend, visit with your kids as an educational tour, and spend a relaxing vacay with your family.
Excellent and nice blog. If anyone is looking for Object oriented programming assignment help, then visit BookMyEssay to get services at an affordable cost.
Top talent recruiting solutions company gives the Recruitment as a Service is at the centre of what we do and constitutes the basis of all of our recruitment services. It indicates that we only ever charge clients based on billed hours, and not a percentage of the wage of the role we are filling.
There are several benefits to using an eyelash extension sealant. One of the most significant benefits is that it helps to extend the life of the eyelash extensions. This means that clients can go longer between touch-up appointments, saving time and money in the long run. Additionally, an eyelash extension sealant can help to protect the extensions from dirt, oil, and other environmental factors that can cause them to break or fall off.
Jewelgalore features a stunning selection of stud earrings . Explore our collection to find elegantly designed pieces that add a touch of sophistication and charm to your style.
Explore the pinnacle of medical education at Osh University, standing proudly among top-tier medicine universities . With a commitment to excellence, Osh provides a transformative experience that molds aspiring medical professionals into leaders of tomorrow.
Jewelgalore presents a striking collection of silver ring for men . Explore our range of elegantly crafted pieces, perfect for adding sophistication and style to men's fashion.
Looking for expert gastrointestinal care? Shalamar Hospital's stomach doctor offers top-notch treatments and consultations, prioritizing your stomach's well-being.
I'm working on hands-on Zigbee hacking workshops, including one with Aurélien Francillon for ToorCamp, focused on advanced stack overflow attacks for MSP430 and AVR microcontrollers. For exceptional space design, check out the top interior fit out companies in Dubai.
Devellux Inc is the parent company behind many well-known essay-writing websites, although most users never realize the connection. Sites such as EssayPro, EssayService, DoMyEssay, and Studyfy operate under different names but follow the same structure and often share internal resources. Devellux relies heavily on SEO-driven content, coordinated branding, and cross-promotion to guide students toward its services without openly disclosing the shared ownership. While the setup appears organized, the lack of transparency makes it hard for students to make informed decisions about which service they’re actually dealing with—and whether the quality is consistent across those brands.
Use our free Mortgage Overpayment Calculator to find out how extra payments could help you pay off your mortgage faster and cut down on total interest costs. See the impact of monthly, annual, or one-time overpayments and plan your finances smarter.
Cardiac Stress Test.Cardiac stress test is one of the most widely employed tools of diagnosis of the health care providers to evaluate the functionality of heart. This painless test assists a physician in analyzing the degree at which the heart responds well to physical exertion or exercise.
Post a Comment