Howdy everybody,
Rob Spanton and Tom Bennellick have recently released fetproxy, an open-source replacement for gdbproxy. They reverse engineered the protocol the week before I did, and their implementation--unlike mine--acts as a replacement for gdbproxy. They also managed to get approval from Texas Instruments, which is quite neighborly indeed.
I'll be closing up my msp430fet project, which was only intended as a stop-gap until Rob and Tom were able to make their release. The final state will be a standalone C client for programming; I won't be adding support for debugging.
--Travis
Friday, March 27, 2009
Sunday, March 15, 2009
Breaking 802.15.4 AES128 by Syringe
by Travis Goodspeed <travis at radiantmachines.com>
I'm working on a pair of hands-on Zigbee hacking workshops. The first, which I've submitted with Aurélien Francillon to ToorCamp involves the writing of advanced stack overflow attacks for the MSP430 and AVR microcontrollers. The second, which I've submitted to Defcon 17, involves a number of hands-on hardware attacks against Zigbee nodes. Both include the sniffing of AES128 keys from a CC2420 Zigbee radio, a procedure that I demonstrated informally at Source Boston and describe below.
The CC2420 is a popular Zigbee/802.15.4 radio, and it is found in many wireless sensor development kits. We'll be attacking its hardware-accelerated AES128 implementation, by taking advantage of the fact that keys must be loaded over the SPI bus.
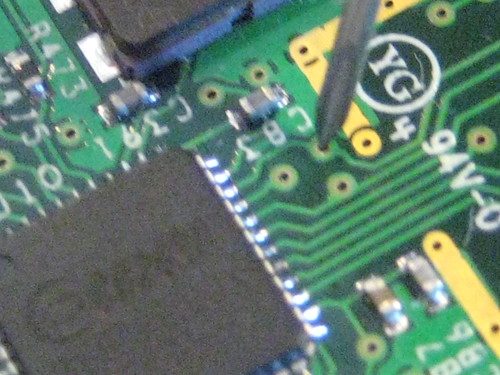
In the photograph above, I've tapped one of three SPI pins of the CC2420 radio chip on a Telos B using a hypodermic syringe. SPI consists of four pins: SCL, MOSI, MISO, and !SS. SCL, the Serial Clock, is output from the master to synchronize communication with the slave. MOSI and MISO are data lins, Master Out Slave In and Master In Slave Out. !SS or Slave Select is an inverted line that indicates the selection of a particular slave chip. Here, we'll only be tapping SCLK and one of the data lines, as two syringes are much easier to hold that four. Ground is shared by USB, so it isn't critical that we tap it.
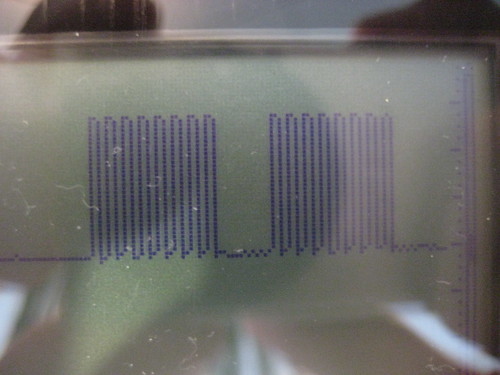
As seen on my portable scope below, the tapped pin is the SCL, the data clock. The clock stands out because it idles low, and because all pulses in a batch are of regular width. Unlike a system clock, the clock only cycles when data is being transported.
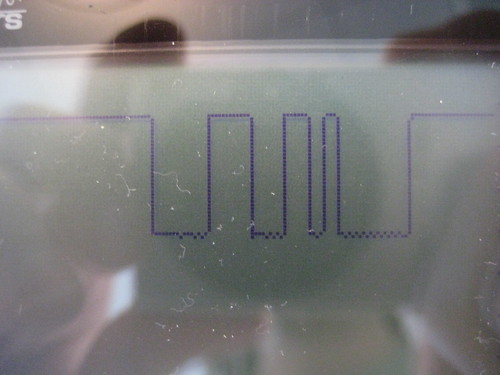
The remaining two pins, in the group of three, are data. As shown on the scope image below, SPI data lines idle high, and bits are measures on edges of the clock.
Now that the clock and data lines have been found, it is necessary to sniff the traffic using a bus adapter. Until SPI-sniffing firmware for the Hackaday Bus Pirate becomes available, I will continue to use the Total Phase Beagle I2C/SPI Protocol Analyzer. A screenshot of the Total Phase client follows.
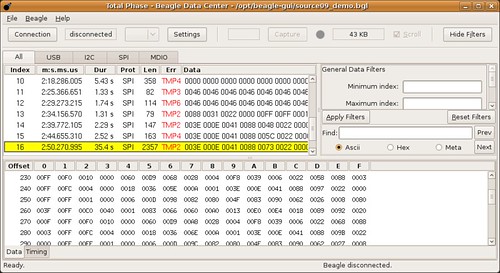
All that remains to identify the key in use, or anything else sent over the bus, is to read the log. I will likely release scripts for doing so at Defcon.
I'm working on a pair of hands-on Zigbee hacking workshops. The first, which I've submitted with Aurélien Francillon to ToorCamp involves the writing of advanced stack overflow attacks for the MSP430 and AVR microcontrollers. The second, which I've submitted to Defcon 17, involves a number of hands-on hardware attacks against Zigbee nodes. Both include the sniffing of AES128 keys from a CC2420 Zigbee radio, a procedure that I demonstrated informally at Source Boston and describe below.
The CC2420 is a popular Zigbee/802.15.4 radio, and it is found in many wireless sensor development kits. We'll be attacking its hardware-accelerated AES128 implementation, by taking advantage of the fact that keys must be loaded over the SPI bus.

In the photograph above, I've tapped one of three SPI pins of the CC2420 radio chip on a Telos B using a hypodermic syringe. SPI consists of four pins: SCL, MOSI, MISO, and !SS. SCL, the Serial Clock, is output from the master to synchronize communication with the slave. MOSI and MISO are data lins, Master Out Slave In and Master In Slave Out. !SS or Slave Select is an inverted line that indicates the selection of a particular slave chip. Here, we'll only be tapping SCLK and one of the data lines, as two syringes are much easier to hold that four. Ground is shared by USB, so it isn't critical that we tap it.
As seen on my portable scope below, the tapped pin is the SCL, the data clock. The clock stands out because it idles low, and because all pulses in a batch are of regular width. Unlike a system clock, the clock only cycles when data is being transported.

The remaining two pins, in the group of three, are data. As shown on the scope image below, SPI data lines idle high, and bits are measures on edges of the clock.

Now that the clock and data lines have been found, it is necessary to sniff the traffic using a bus adapter. Until SPI-sniffing firmware for the Hackaday Bus Pirate becomes available, I will continue to use the Total Phase Beagle I2C/SPI Protocol Analyzer. A screenshot of the Total Phase client follows.

All that remains to identify the key in use, or anything else sent over the bus, is to read the log. I will likely release scripts for doing so at Defcon.
Wednesday, March 4, 2009
NeighborCon
Howdy y'all,
The NeighborCon announcement is up, for Knoxville's most neighborly hacker conference. There's also talk of a trip to Dollywood after the conference has concluded.
--Travis Goodspeed
<travis at radiantmachines.com>
The NeighborCon announcement is up, for Knoxville's most neighborly hacker conference. There's also talk of a trip to Dollywood after the conference has concluded.
--Travis Goodspeed
<travis at radiantmachines.com>
Tuesday, March 3, 2009
New Business Card
Howdy Neighbors,
I've just received a few prototypes of my new business card, which also happens to be a 1.8V/3.3V smart card emulator. (Most readers default to 5V, just to make life difficult.) The final revision will be compatible with all three voltages, and I expect to order boards in quantity by the end of next month.

--Travis Goodspeed
<travis at radiantmachines.com>
Postscript:
Just to be perfectly clear, these are not intended for TV piracy and they are not for sale.
I've just received a few prototypes of my new business card, which also happens to be a 1.8V/3.3V smart card emulator. (Most readers default to 5V, just to make life difficult.) The final revision will be compatible with all three voltages, and I expect to order boards in quantity by the end of next month.

--Travis Goodspeed
<travis at radiantmachines.com>
Postscript:
Just to be perfectly clear, these are not intended for TV piracy and they are not for sale.
Subscribe to:
Comments (Atom)
